Now that Work-from-home is the new normal
The pandemic created a here to stay operational culture of work from home. This became a welcome economic adaptation most companies have established. We have the wisdom to lnspect, correlate and understand multiple threats. To mitigate data security risks in the current remote work era, Proktor by JIFFY.ai is empowering you with Employee Security Profiling, Real-Time Screen Monitoring and Assessment of Incidents and Remediation. The world’s brightest minds are now here to empower you in anticipating the most sophisticated attacks on the endpoint and beyond.
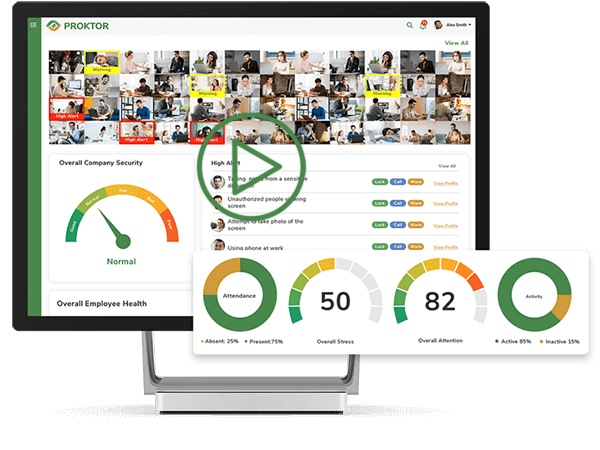
What is Proktor
Covid Ready Surveillance
Proktor - Making Work From Home The New Normal
Centuries back, when the bubonic plague swept through Europe, people in larger cities were told to stay home for a month. Times were such that only an individual from an uninfected household could venture outside to grab supplies. The situation is synonymous to the 2019 COVID outbreak.
In the grip of the Covid-19 pandemic, the advice is the same – Stay home and avoid physical contact.

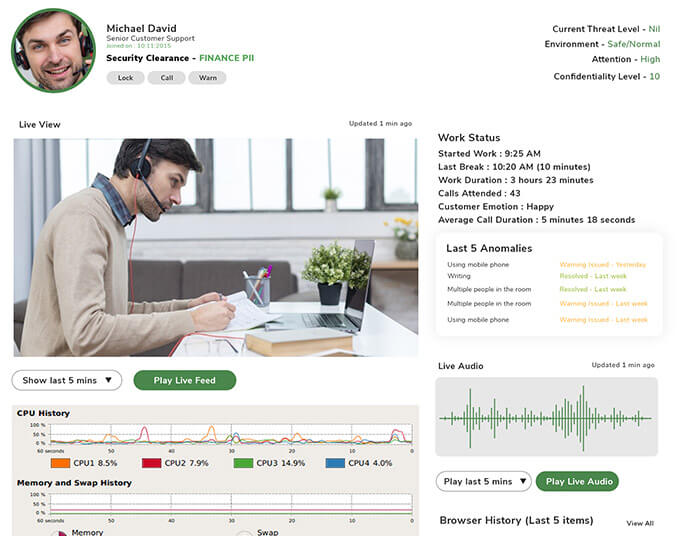
Corporate Surveillance For Work From Home Workforce
After the ease of lockdown across the globe, thousands of companies adapted to the use of monitoring software to record employees’ Web browsing and active work hours. In short, tracking their productivity to ensure work happens despite the remote access. Proktor AI offers Virtual Secure Workspaces
- Centralized Monitoring
- Intuitive Dashboard Surveillance
- Real-time Employee Profiling & Assessment
- AI-led threat detection to avoid data leaks
- Employee Health Monitoring via thermal cameras
- FaceReko Attendance Management
DON'T MISTAKE IT WITH WORK POLICING
Our Fair Surveillance Software-Monitoring when working remotely

What we’re simply doing is monitoring keystrokes, email, file transfers, applications used,and tracking the time the employee gives to each task. We help the management know what is on the employee’s screen. This moderate monitoring is highly recommended for brands that work on guarded data.
What's More (Employee benefit)

Besides keeping company employees in line with their productivity, our technology tracks the overall employee health too.
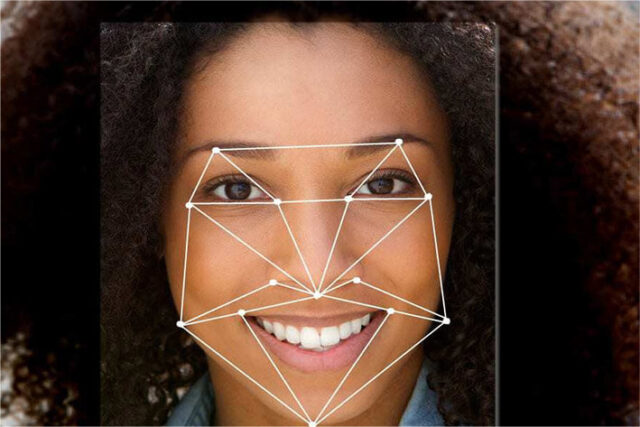
Use of ________ to monitor the health of workers takes us one step ahead of the competition in our space. Developing a facial-recognition feature that could display a worker’s real-world emotion is work of genius